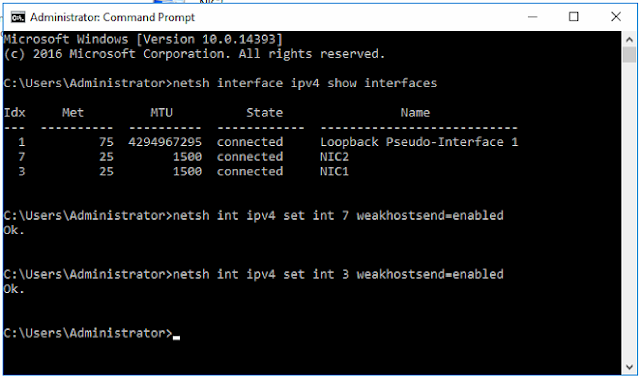
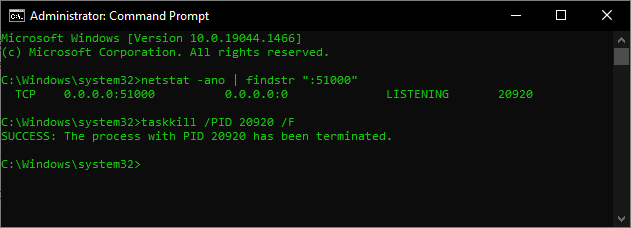
How can the simple parity bit detect a damaged data unit? The simple parity bit can detect a damaged data unit by ensuring that the total number of bits set to 1 (or sometimes 0, depending on the parity system) in the data unit, including the parity bit itself, is either even or odd. Here's how it works: Adding Parity Bit : Before transmission, a parity bit is added to the data unit. This parity bit is calculated based on the current state of the data unit. If using even parity, the parity bit is set so that the total number of 1-bits in the data unit (including the parity bit) is even. If using odd parity, the parity bit is set so that the total number of 1-bits in the data unit (including the parity bit) is odd. Transmission : The data unit, along with the parity bit, is transmitted. Reception : Upon reception, the receiving system recalculates the parity of the received data unit, including the received parity bit. Error Detection : If the recalculated parity doesn't mat...